In today’s interconnected and digitalized world, the security of business data and assets has become paramount. Cyber threats are evolving rapidly, and traditional security measures are no longer sufficient to protect sensitive information.
As a response to this shifting landscape, the concept of Zero Trust has emerged as a powerful security strategy. But what exactly does the Zero Trust model mean, and how can you build a compelling business case for investing in such a strategy? Let’s delve into the details and decode the essence of Zero Trust for your business.
What is Zero Trust?

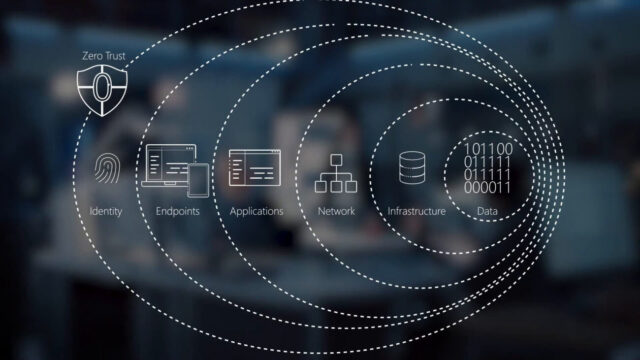
Zero Trust is a security model that operates under the assumption that no user or device should be trusted implicitly, regardless of their location or level of access. This approach stands in stark contrast to the traditional perimeter-based security model, where once a user gains access to a network, they are generally trusted to move freely within it.
Zero Trust can be likened to the idea of “verifying before trusting.” It is similar to how we conduct real-world interactions, especially with strangers. When meeting someone new, we don’t automatically trust them with sensitive information or valuable assets. Instead, we cautiously verify their identity, intentions, and credibility before sharing anything significant or granting them access to restricted areas.
Similarly, the Zero Trust model requires businesses to continually authenticate and validate users and devices, irrespective of whether they are inside or outside the organization’s network. It emphasizes the need for multi-layered security measures, constantly reassessing access privileges, and scrutinizing each interaction to prevent potential security breaches.
How to Build a Business Case for Investment in Zero Trust

Assessing the Current Security Landscape
Begin by evaluating your organization’s existing security infrastructure and identify any vulnerabilities or limitations in the current approach. Highlight recent security incidents or data breaches to underscore the importance of staying ahead of evolving threats.
Articulating the Business Impact
Clearly communicate the potential consequences of a security breach in terms of business risk, financial losses, brand reputation damage, legal liabilities, and customer trust erosion. These tangible risks can help decision-makers grasp the need for a robust security strategy like Zero Trust.
Emphasizing the Evolving Perimeter
With the rise of remote work, mobile devices, and cloud services, the traditional network perimeter has blurred. Employees, clients, and partners access resources from various locations and devices, making a perimeter-centric security approach obsolete. Zero Trust aligns with this changing paradigm, providing a more adaptable and resilient security model.
Demonstrating Compliance Requirements
Many industries and regions have specific data protection and privacy regulations that businesses must adhere to. Zero Trust helps in achieving and maintaining compliance with these requirements by implementing strict access controls, data encryption, and continuous monitoring.
Quantifying Potential Cost Savings
While implementing a Zero Trust strategy requires investment, it’s essential to highlight the potential cost savings in the long run. By preventing data breaches and security incidents, businesses can avoid costly recovery efforts and mitigate the financial fallout associated with cyberattacks.
Conveying the Value of a Zero Trust Strategy

Improved Data Protection
Emphasize that Zero Trust significantly reduces the attack surface by limiting access to sensitive data. Even if a breach occurs, the damage can be contained due to restricted access.
Enhanced Productivity
Contrary to the belief that robust security hinders productivity, Zero Trust can actually boost efficiency. It enables secure access to resources from any location, promoting flexible work arrangements without compromising security.
Preserving Customer Trust
Customers place a high value on the security and privacy of their data. A Zero Trust approach demonstrates a commitment to safeguarding customer information, fostering trust, and potentially attracting more clients.
Future-Proofing the Business
Technology evolves rapidly, and so do cyber threats. Zero Trust, as a dynamic and adaptive security model, equips the business to better withstand emerging threats and security challenges in the future.
Competitive Advantage
Embrace Zero Trust as a proactive measure to stay ahead of competitors. Demonstrating a strong security posture can be a unique selling point, particularly when dealing with security-conscious customers and partners.
Zero Trust isn’t just a security buzzword — it’s a strategic and forward-thinking approach to protect your business in an ever-evolving digital landscape. By understanding Zero Trust and building a compelling business case for it, you can gain the necessary support and investment to implement a Zero Trust strategy within your organization effectively.